Turtle
被改过的upx壳,但是把ADD改成UPX也还是脱不了壳。只能手动脱壳
手动脱壳
用x64dbg打开。

运行到这里,使用Scylla进行dump,然后IAT自动搜索,获取导入,修复转储。获得Turtle_dump_SCY.exe
分析程序
int __fastcall main(int argc, const char **argv, const char **envp)
{
char v4[256]; // [rsp+20h] [rbp-60h] BYREF
char v5[48]; // [rsp+120h] [rbp+A0h] BYREF
char Buf1[46]; // [rsp+150h] [rbp+D0h] BYREF
char Buf2[5]; // [rsp+17Eh] [rbp+FEh] BYREF
char v8[2]; // [rsp+183h] [rbp+103h] BYREF
unsigned __int8 Source[8]; // [rsp+185h] [rbp+105h] BYREF
unsigned __int8 Dest[8]; // [rsp+18Dh] [rbp+10Dh] BYREF
char v11[11]; // [rsp+195h] [rbp+115h] BYREF
unsigned int v12; // [rsp+1A0h] [rbp+120h]
int v13; // [rsp+1A4h] [rbp+124h]
int v14; // [rsp+1A8h] [rbp+128h]
unsigned int v15; // [rsp+1ACh] [rbp+12Ch]
sub_401C20(argc, argv, envp);
strcpy(v11, "yekyek");
Buf2[0] = -51;
Buf2[1] = -113;
Buf2[2] = 37;
Buf2[3] = 61;
Buf2[4] = -31;
qmemcpy(v8, "QJ", sizeof(v8));
v5[0] = -8;
v5[1] = -43;
v5[2] = 98;
v5[3] = -49;
v5[4] = 67;
v5[5] = -70;
v5[6] = -62;
v5[7] = 35;
v5[8] = 21;
v5[9] = 74;
v5[10] = 81;
v5[11] = 16;
v5[12] = 39;
v5[13] = 16;
v5[14] = -79;
v5[15] = -49;
v5[16] = -60;
v5[17] = 9;
v5[18] = -2;
v5[19] = -29;
v5[20] = -97;
v5[21] = 73;
v5[22] = -121;
v5[23] = -22;
v5[24] = 89;
v5[25] = -62;
v5[26] = 7;
v5[27] = 59;
v5[28] = -87;
v5[29] = 17;
v5[30] = -63;
v5[31] = -68;
v5[32] = -3;
v5[33] = 75;
v5[34] = 87;
v5[35] = -60;
v5[36] = 126;
v5[37] = -48;
v5[38] = -86;
v5[39] = 10;
v15 = 6;
v14 = 7;
v13 = 40;
j_printf("plz input the key: ");
j_scanf("%s", Source);
j__mbscpy(Dest, Source);
v12 = 7;
sub_401550(v11, v15, v4);
sub_40163E(Source, v12, v4);
if ( !j_memcmp(Source, Buf2, v14) )
{
j_printf("plz input the flag: ");
j_scanf("%s", Buf1);
*&v11[7] = 40;
sub_401550(Dest, v12, v4);
sub_40175A(Buf1, *&v11[7], v4);
if ( !j_memcmp(Buf1, v5, v13) )
j_puts(Buffer);
else
j_puts(aWrongPlzTryAga);
}
else
{
j_puts(aKeyIsWrong);
}
return 0;
}先输入一个key,然后key进行rc4
解密后得到下一轮的key
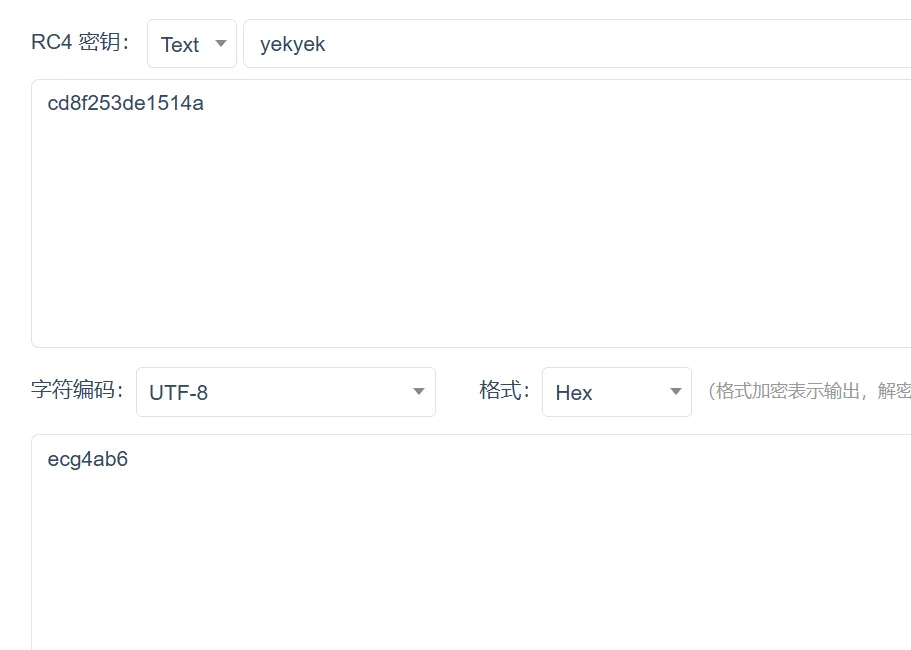
ecg4ab6
第二轮rc4是魔改的xor变成了-=
解密代码改成+=
def rc4_decryp1(cipher, key):
S = list(range(256))
j = 0
# KSA
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
# PRGA
i = j = 0
plain = []
for byte in cipher:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = S[(S[i] + S[j]) % 256]
plain.append((byte + k)%256)
return bytes(plain)然后得到flag
hgame{Y0u’r3_re4l1y_g3t_0Ut_of_th3_upX!}
Thanks for reading!